SunnyStation (Malware Traffic Analysis)
Reference:
https://www.malware-traffic-analysis.net/2022/02/23/index.html
SCENARIO
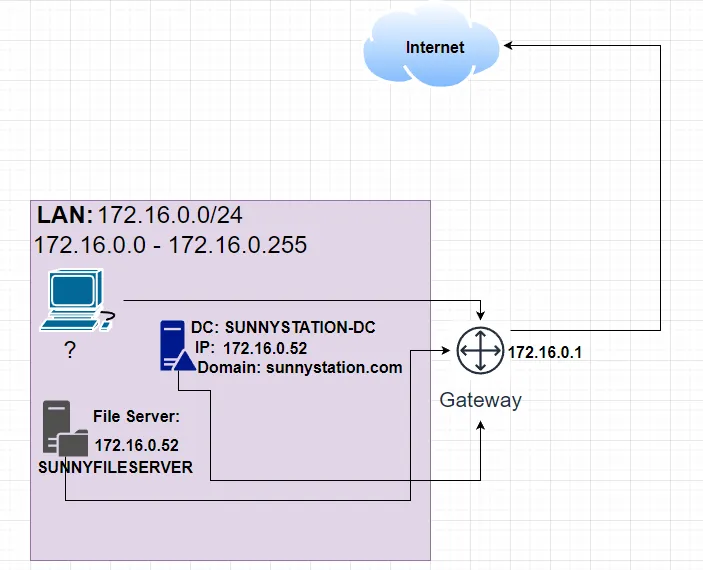
LAN segment data:
|
|
We will start adding more to this topology as we investigate.
The aim of this incident response report
|
|
- RITA/ZEEK
- BRIM
- OSINT Tools (AlienVault, VT, HybridAnalysis, etc…)
We will use more tools as we go along, but for now, these are the tools I plan on using.
First thing first, Let’s go for the low-hanging fruits. We can first start looking at the alerts.
When we first open our pcap using the brim. We see that we got alerts of MALWARE FormBook. That is one of our goals completed (What type of malware are they infected with).
Let’s hone in on the alerts by using this query:
event_type=="alert" | sort -r ts

Let’s focus on the traffic that was flagged as MALWARE FormBook.
Query:
|
|
Now, the following information we’re looking for is where the traffic is from and where it is going.
|
|
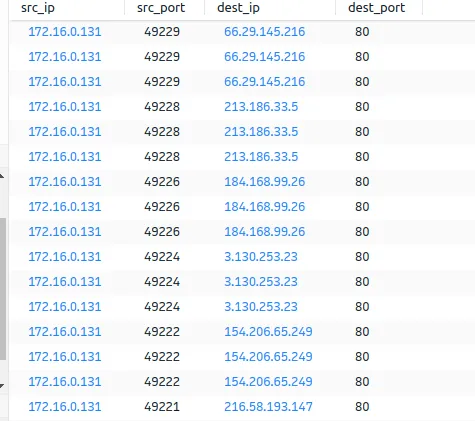
From a glance, we can see that most of this traffic is from: 172.16.0.131.
Let’s get a list of only the destination.
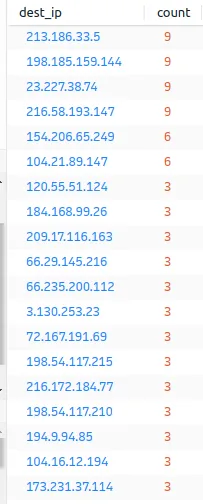
213.186.33.5, 198.185.159.144, 23.227.38.74, and 216.58.193.147 are the most important destinations.
Let the map get the hostname of each destination IP
Here’s the IP:
|
|
Now, let’s go to our HTTP.log and only show results that match our destination IP
|
|
This is what we get; as you can see, it only shows results that match the destination IP. Since this is an eyesore, we can filter it to show only the dest_ip and the host.
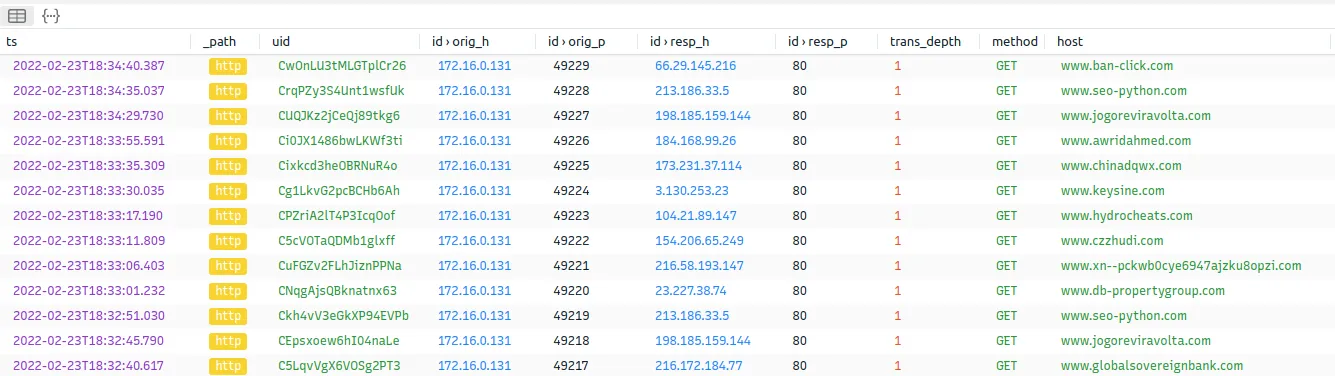
Query:
|
|
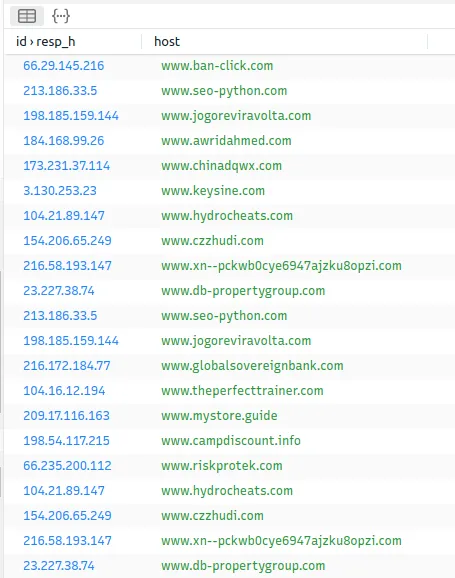
Since some queries are repeated, we can sort them and count how many times it was searched.
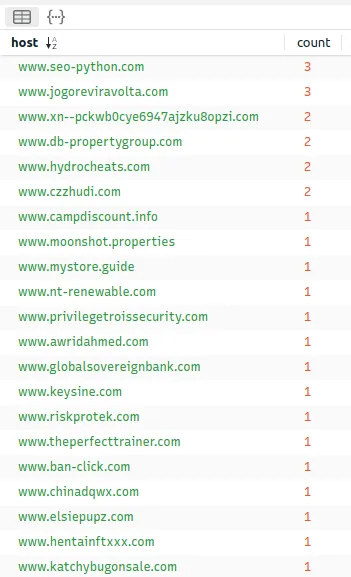
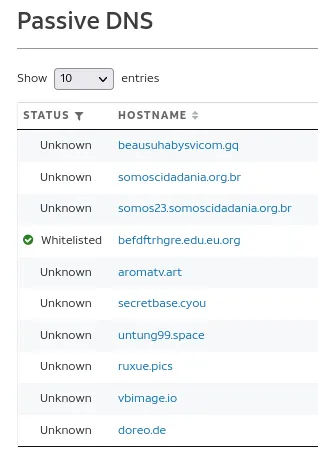
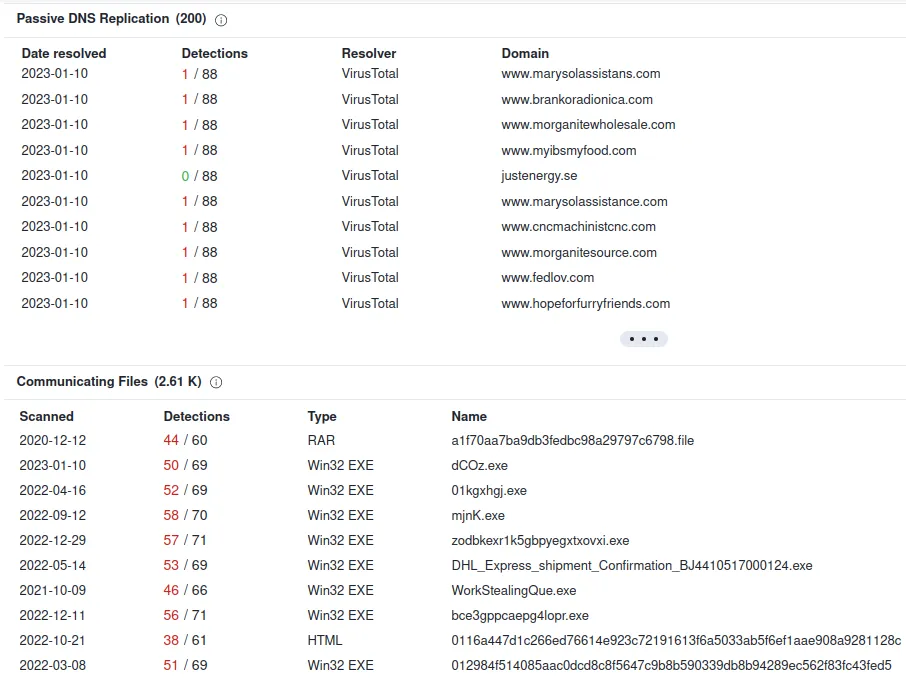
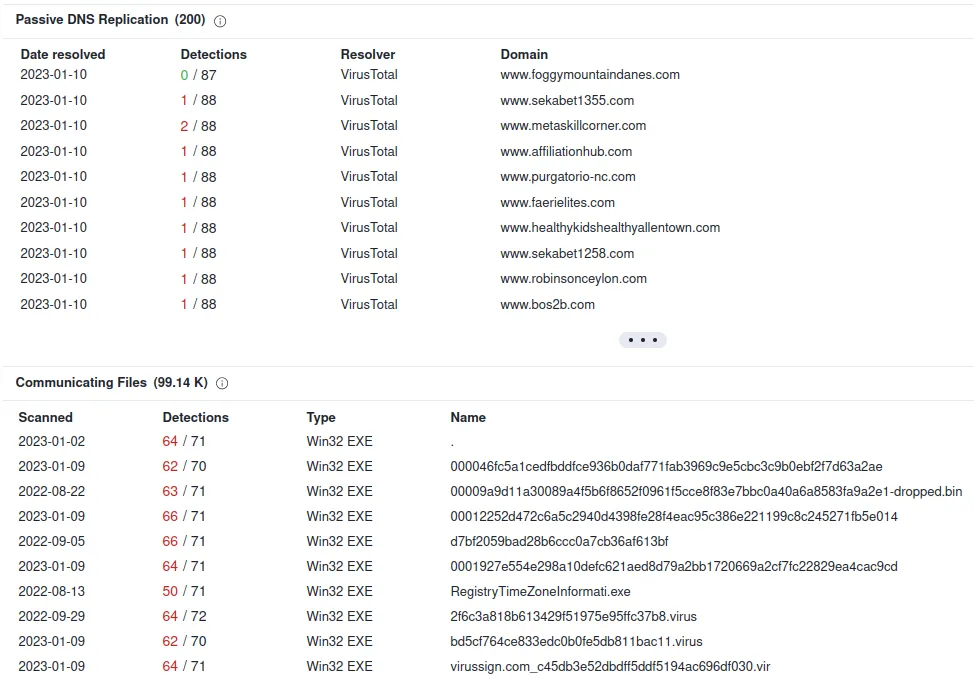
There we go. We got our domains. Next, We can use our OSINT tools to see if these domains are known to host malicious content.
Here are some OSINT tools we can use:
Reference: https://www.activecountermeasures.com/hunt-training/
|
|
Since most of these OSINT tools require IP… I think it helps that I provide them to you.
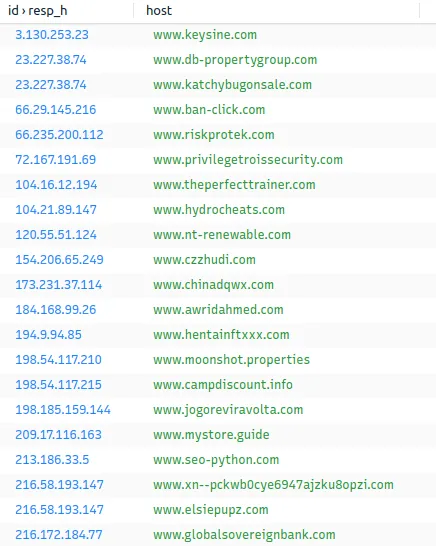
I will be checking www.seo-python.com.
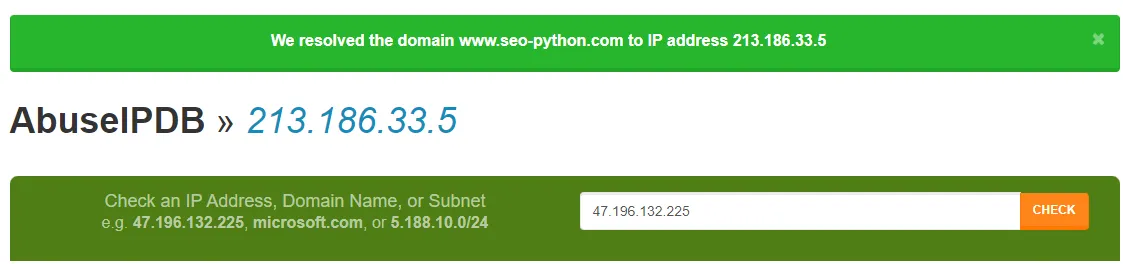
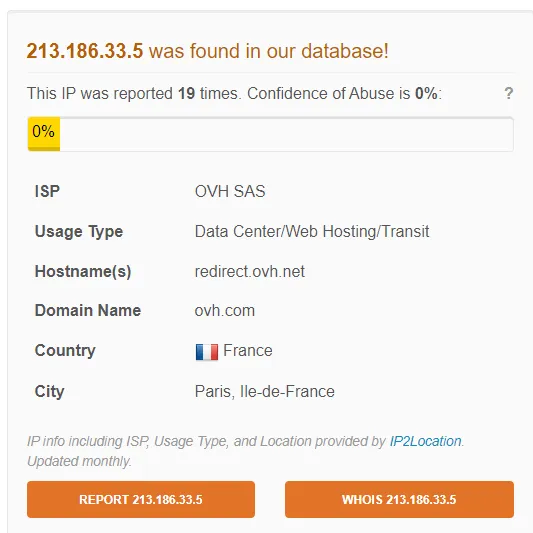
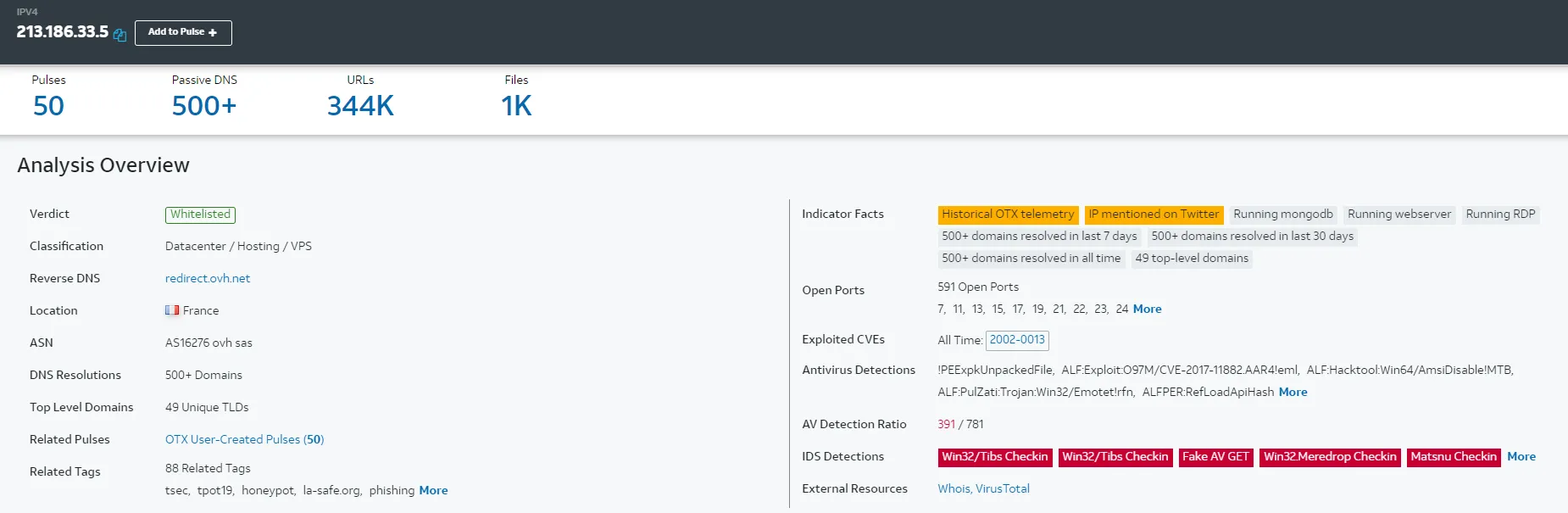
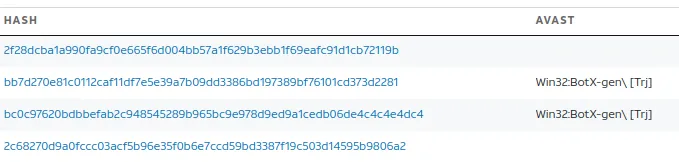
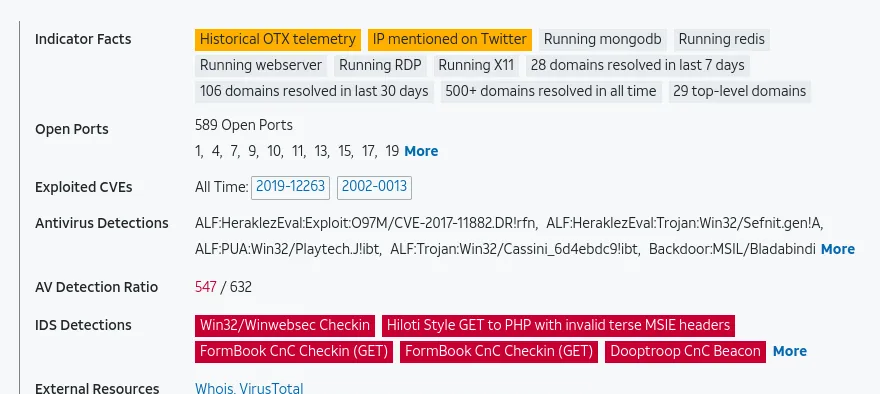
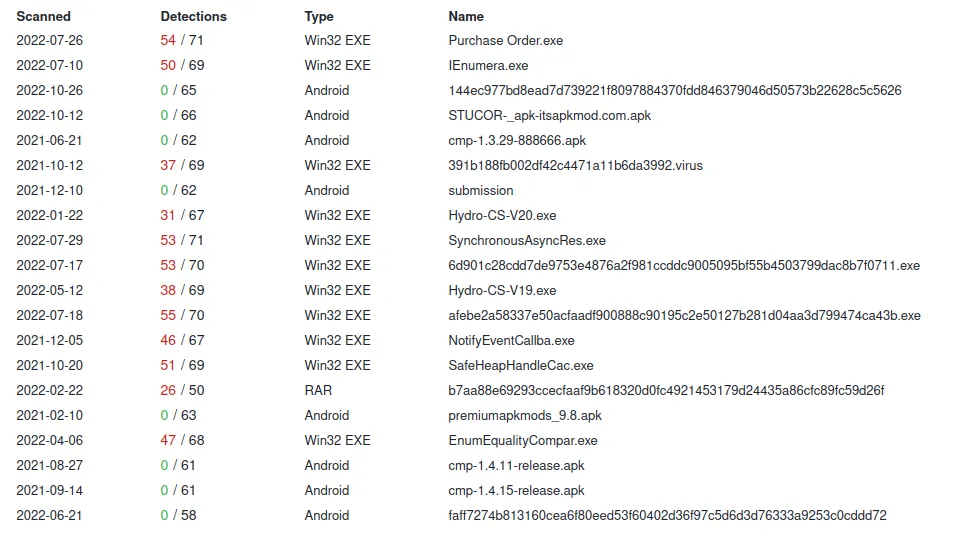
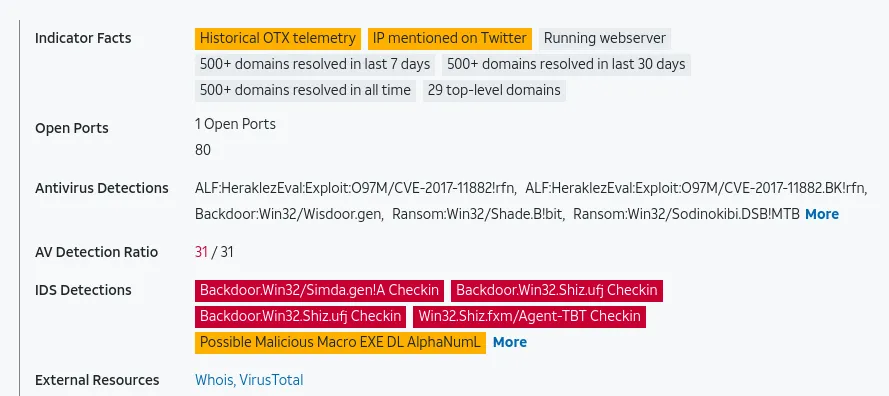
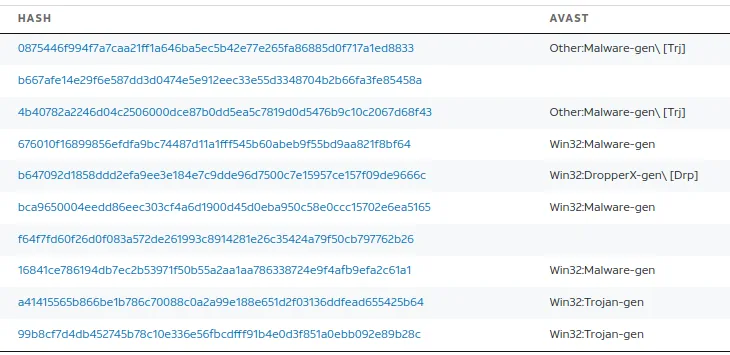
391 / 781? Wow, that’s bad, and Anti-Virus Detection is picking up so many viruses that use this domain. Let’s try another OSINT site, even though we already know the outcome.
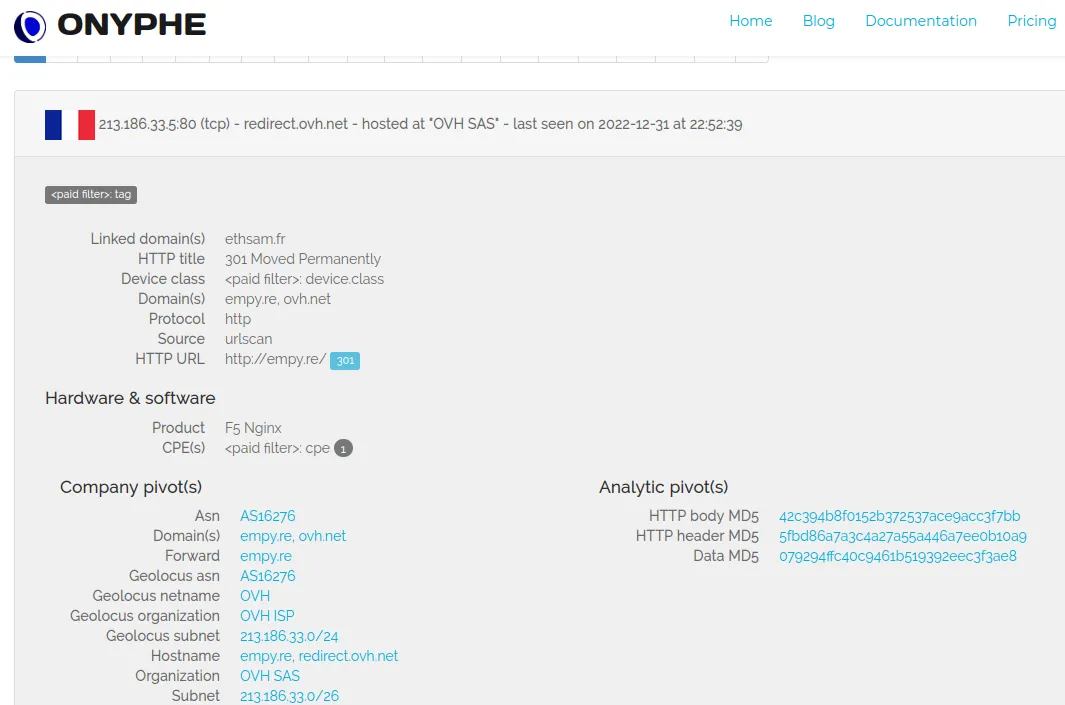
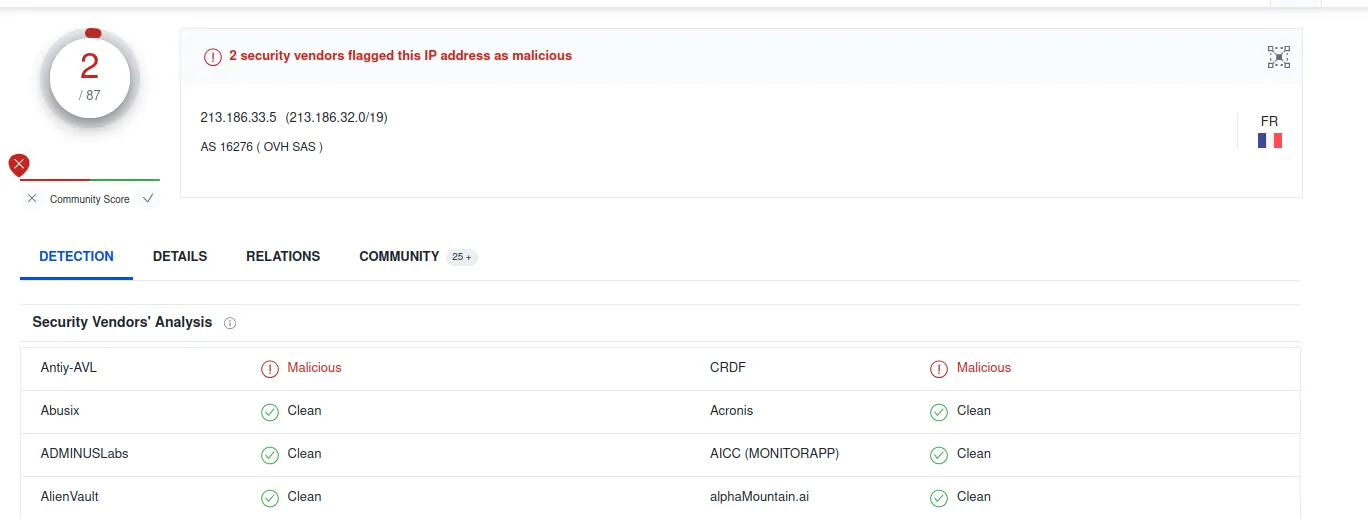
Hosting a lot of malicious .exe
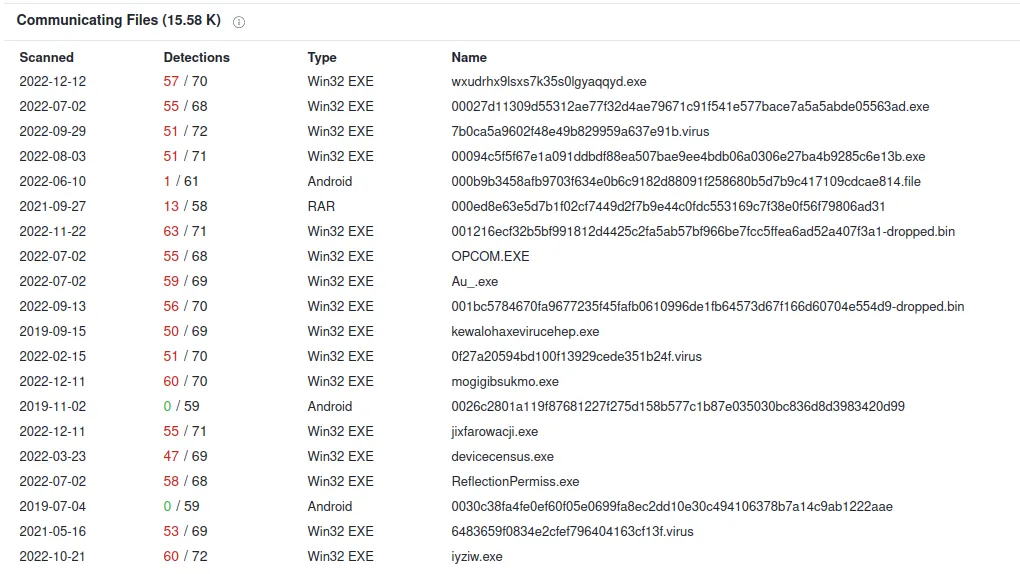
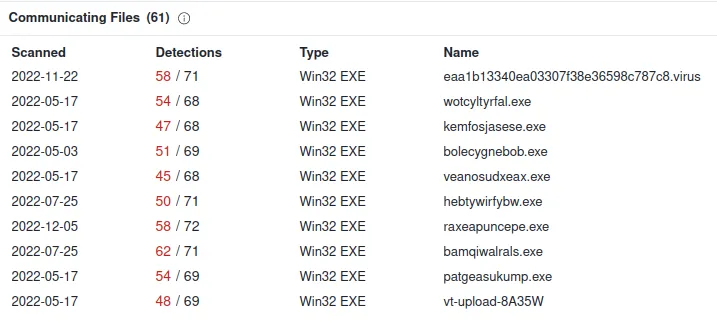
We can conclude that seo.python.com is malicious. We will repeat these searches for all of the domains.
For the sake of the length of this blog, I will not show you the whole process. However, I will show you the final verdict of each domain that we listed.
Additionally, one thing I want to point out is an IOC (Indicator of Compromise of Formbook). The IOC of the formbook is URI syntax: /…./
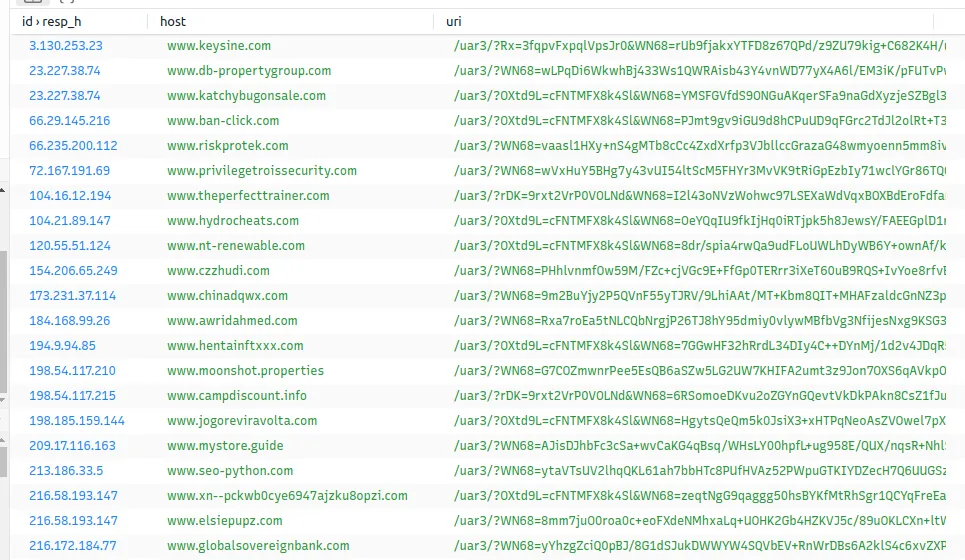
In our case, it: is /uar3/. However, there is a variety of Formbook. Each with its own different URI. For example: In this youtube video, the creator of this video ran into a formbook that was using /e8bw/ similar to what we have.
Alright, let’s investigate the rest of the domain.
Valuating Domain:
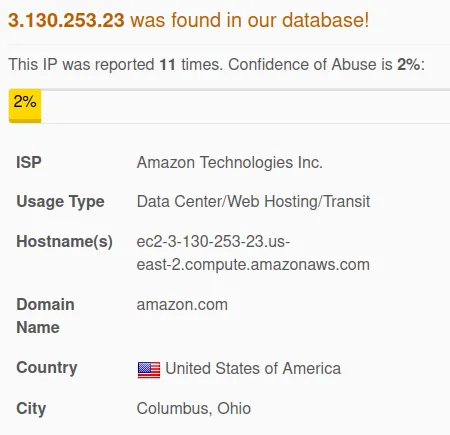
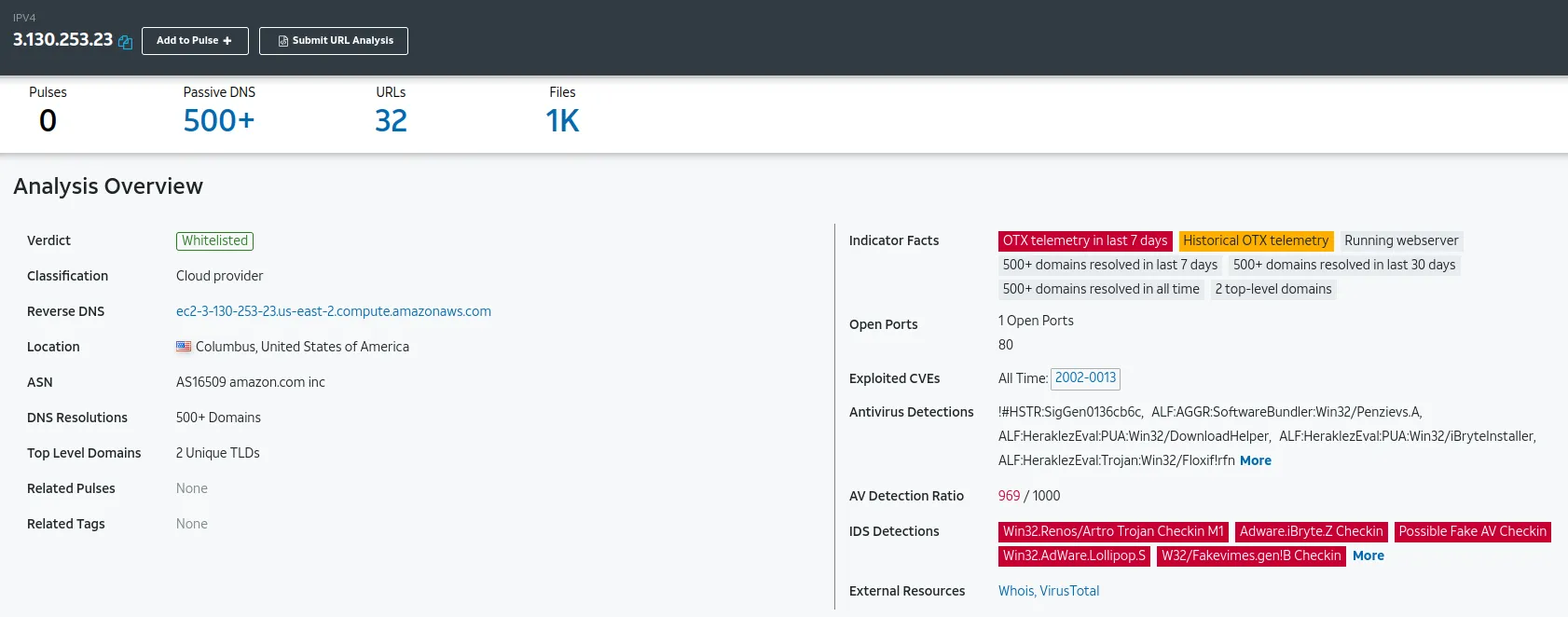
www[.]keysine[.]com
IP: 3.130.253.23
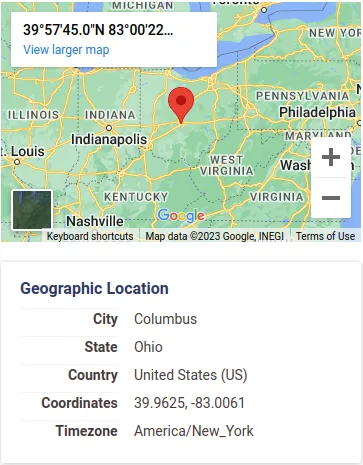
We can ask ourselves whether we have any business in Ohio Columbus. If not, then… our connection should not be going over there.
VirusTotal: Bad
Even though the domain is clean
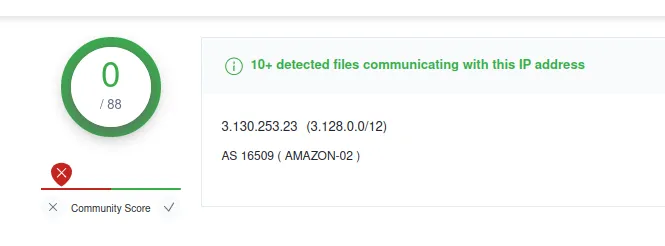
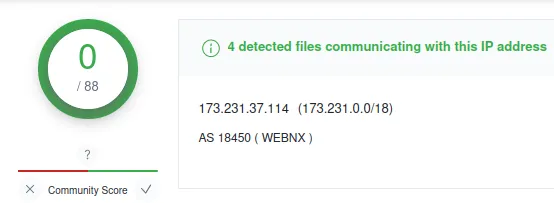
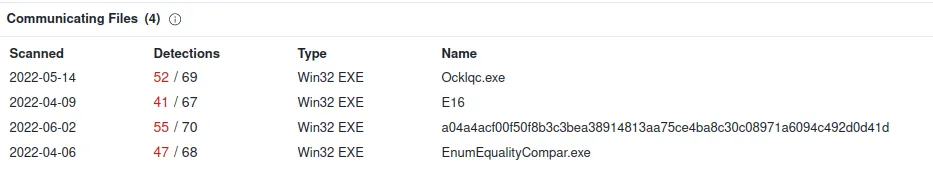
It is still communicating with these malware files…
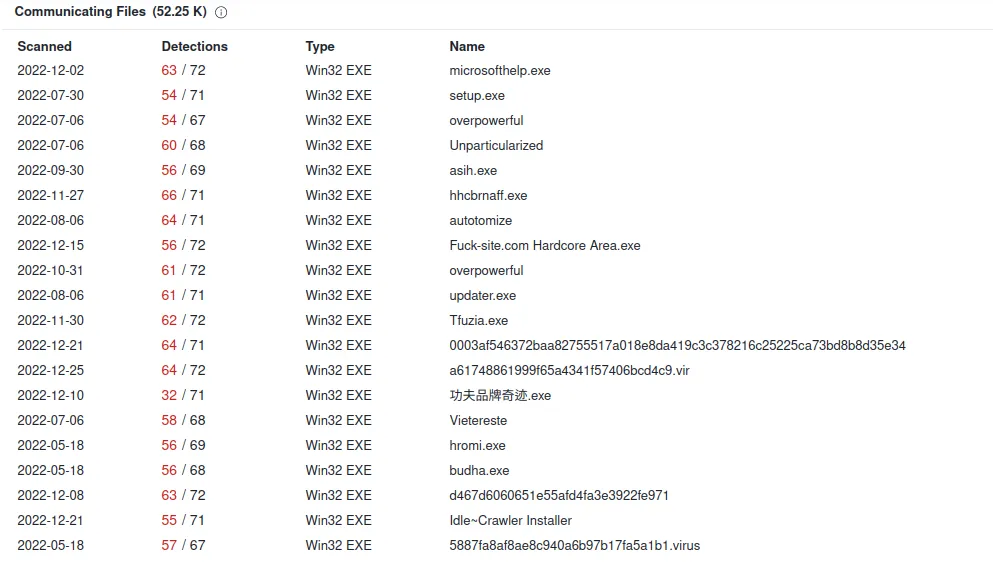
Verdict: Bad
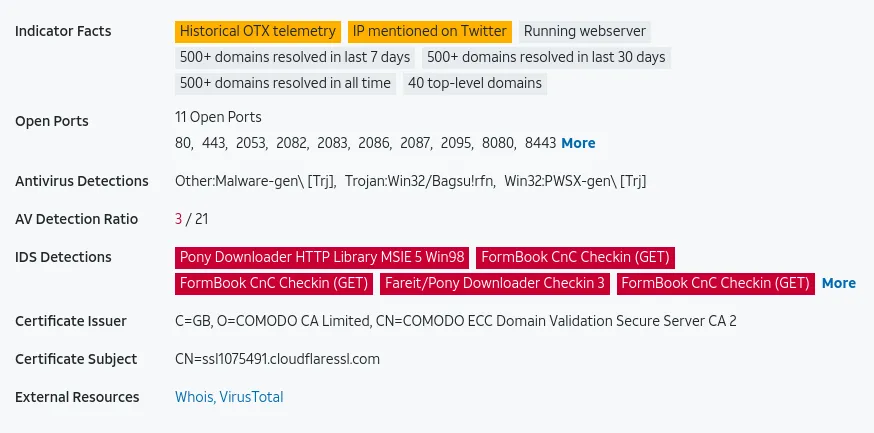
www[.]db-propertygroup[.]com
www[.]katchybugonsale[.]com
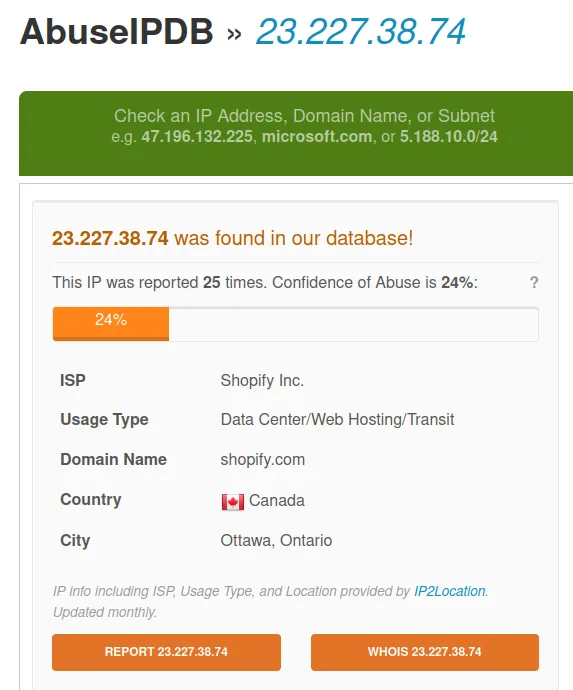
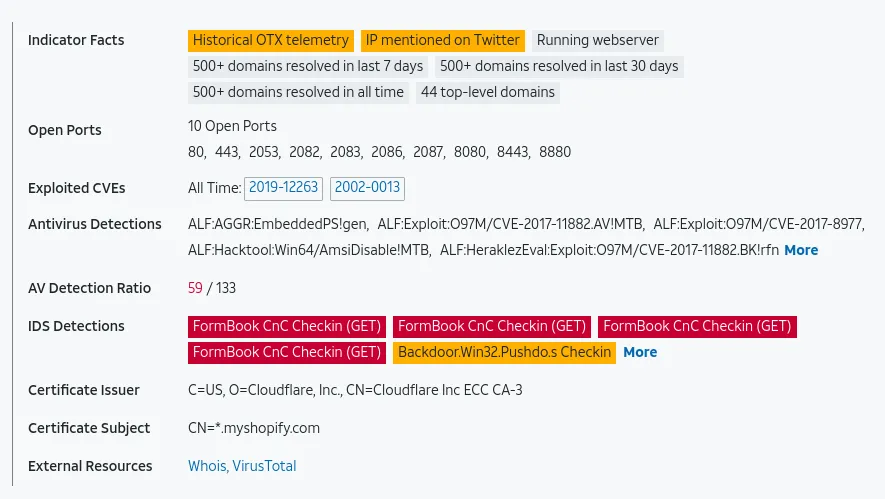
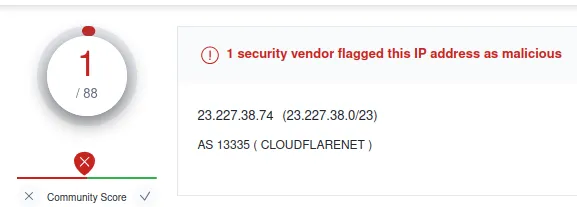
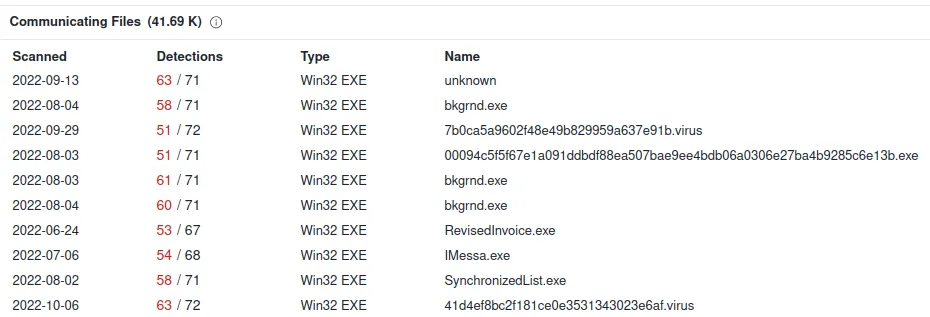
IP: 23.227.38.74
Verdict: Bad
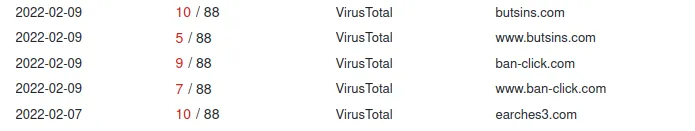
www[.]ban-click[.]com
We can see the associated URL link to this domain.
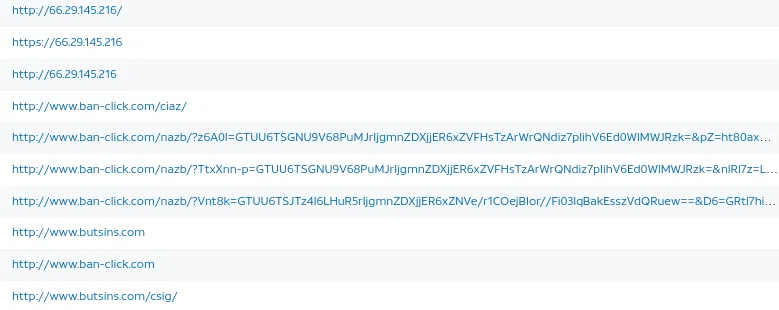
For example:
hxxp[://]www[.]ban-click[.]com/nazb/?z6A0I=GTUU6TSGNU9V68PuMJrIjgmnZDXjjER6xZVFHsTzArWrQNdiz7pIihV6Ed0WlMWJRzk=&pZ=ht80axMpghz was flagged. So it is essential to analyze the other URL that it is associated with.
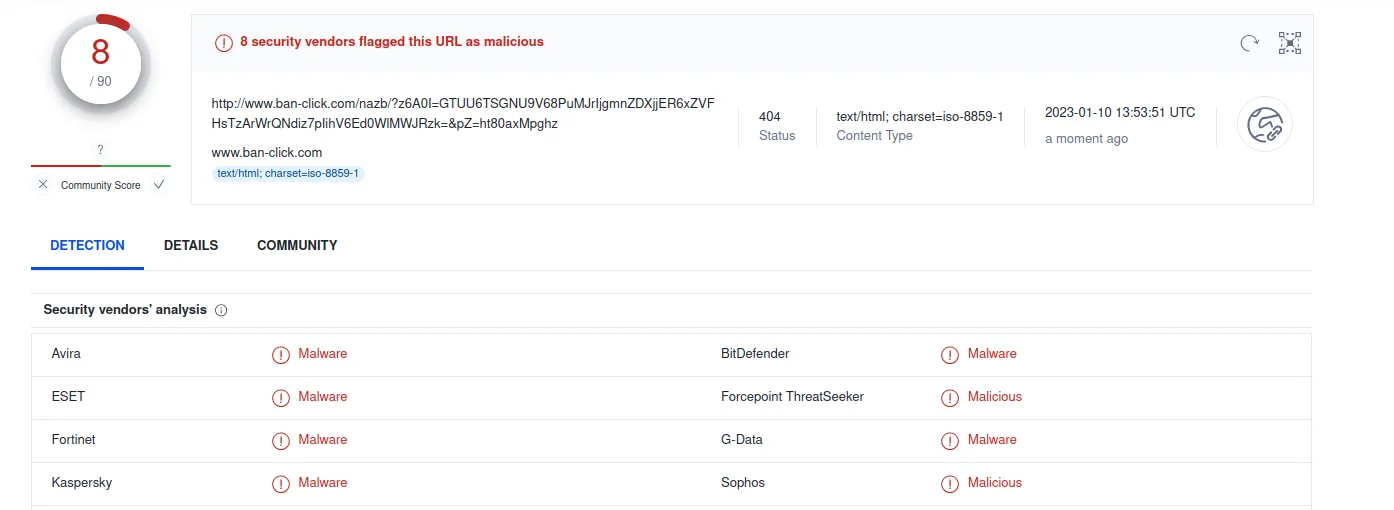
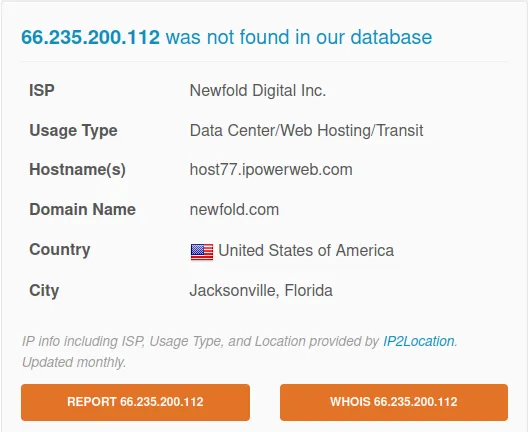
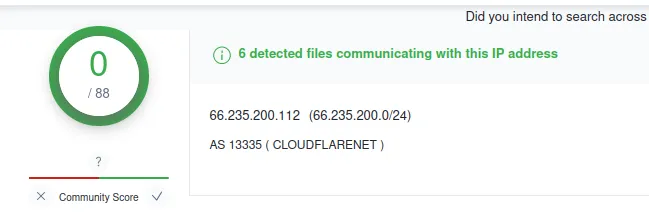
www[.]riskprotek[.]com
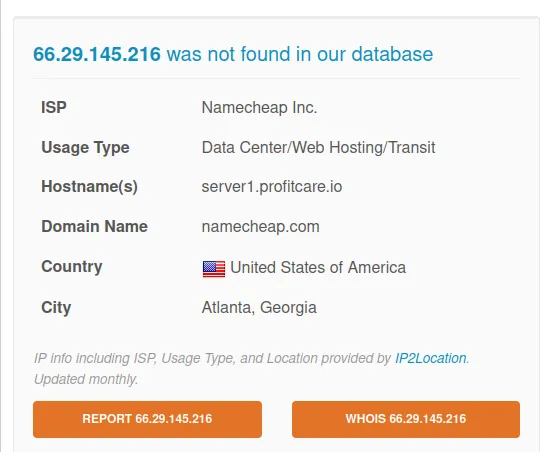
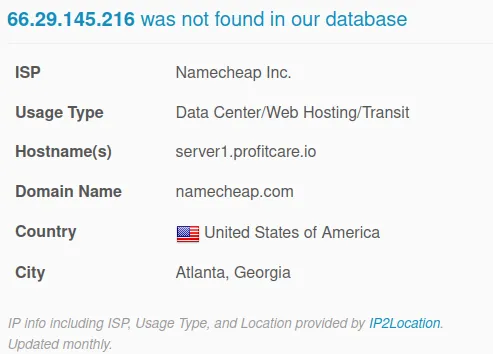
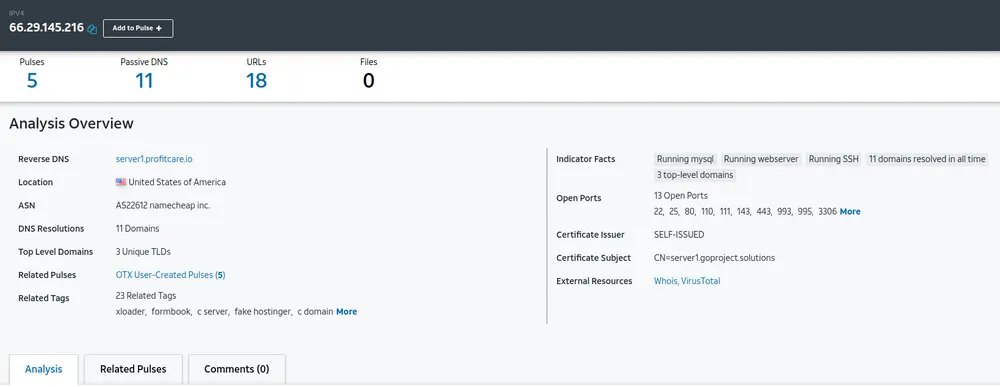
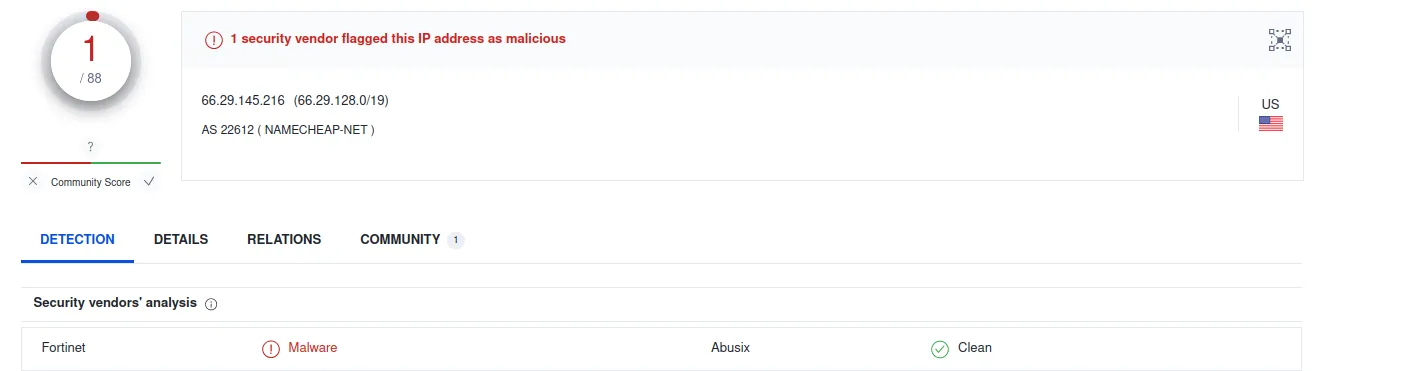
IP: 66.235.200.112
Verdict: Bad
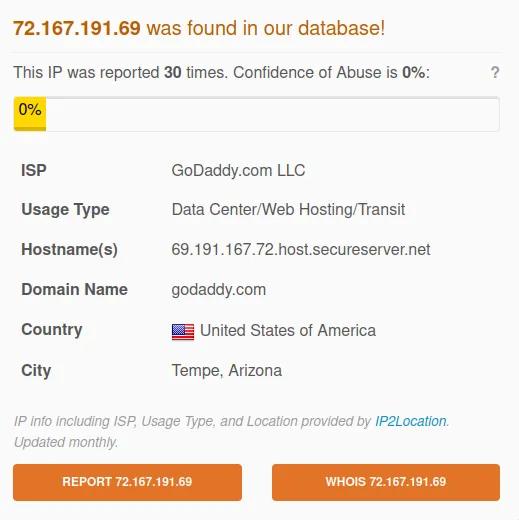
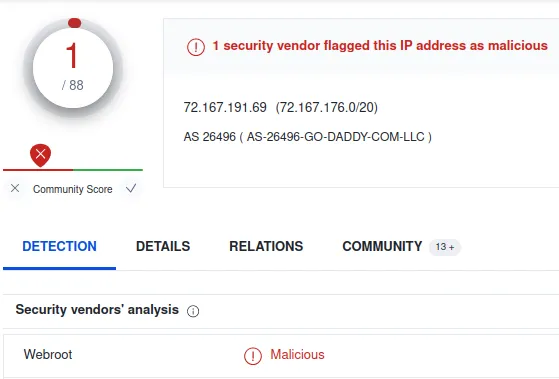
www[.]privilegetroissecurity[.]com
IP: 72.167.191.69
It’s essential to see what the reporter says in the comment to ensure it is a valid response.
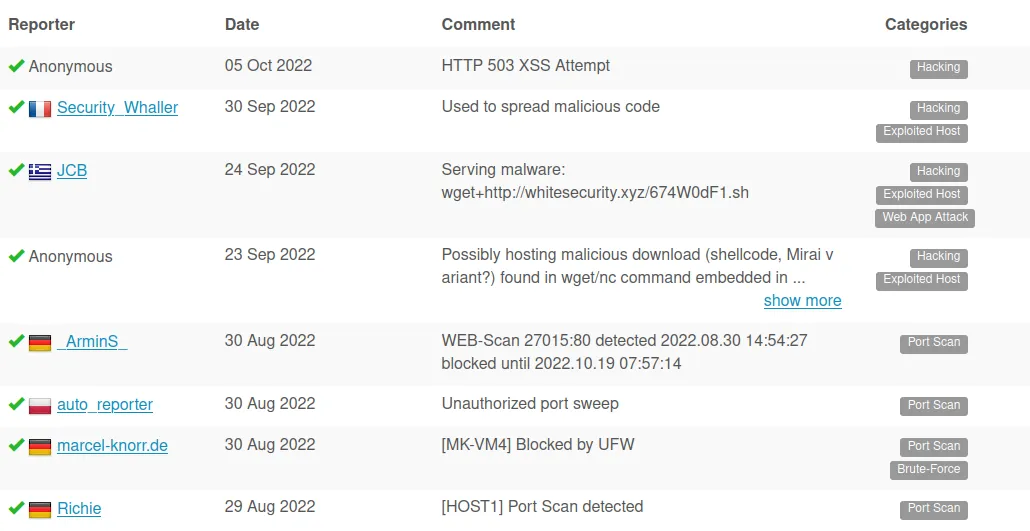
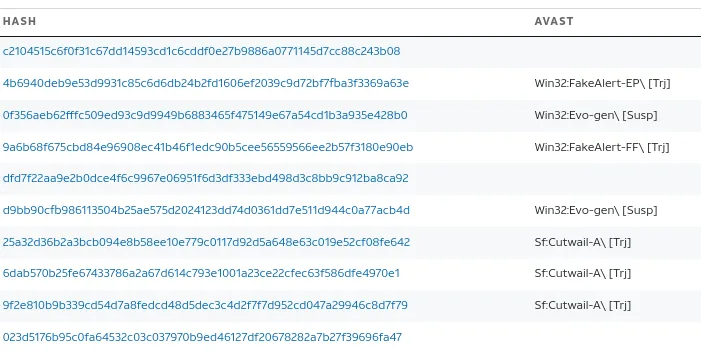
Verdict: Bad
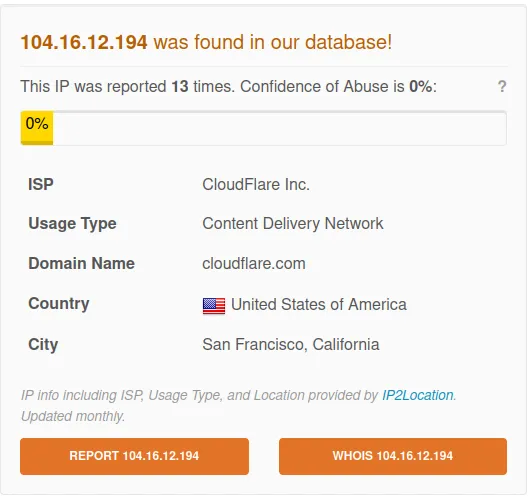
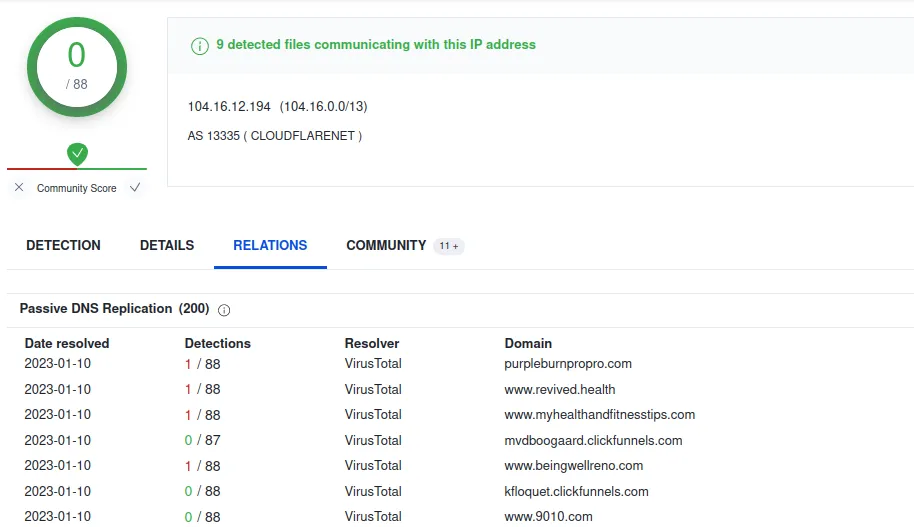
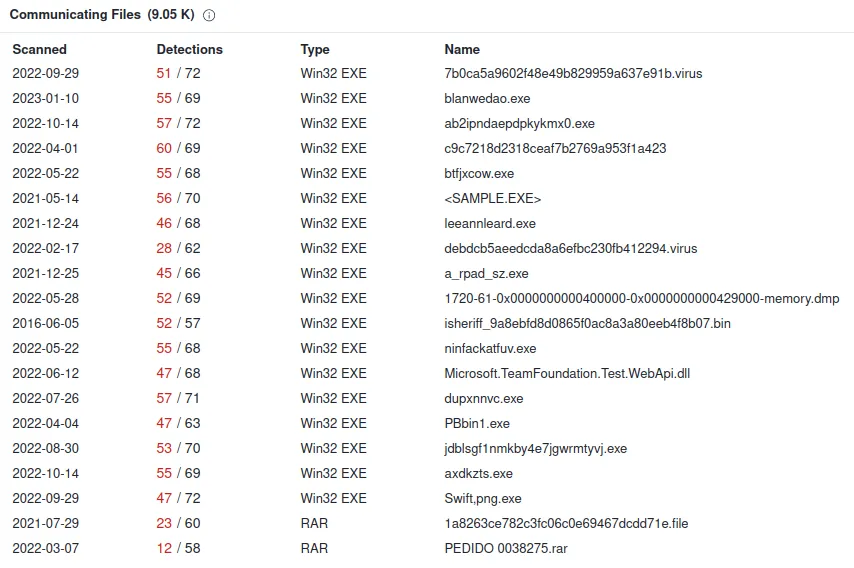
www[.]theperfecttrainer[.]com
IP: 104.16.12.194
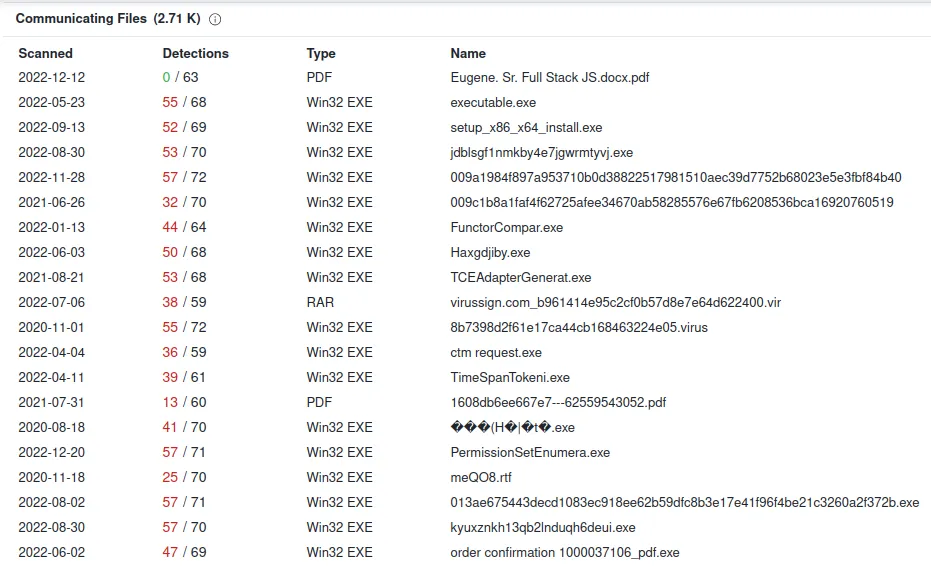
Verdict: Bad
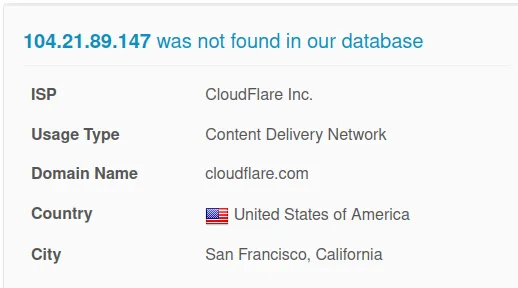
www[.]hydrocheats[.]com
IP: 104.21.89.147
After looking at the DNS and URLs, I don’t see anything suspicious.
Verdict: Bad
www[.]nt-renewable[.]com
IP: 120.55.51.124
AbuseIPDB: Normal (But suspicious if we don’t have any business in china)
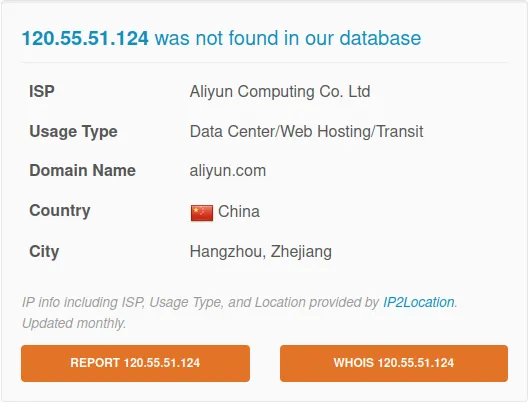
Verdict: Bad
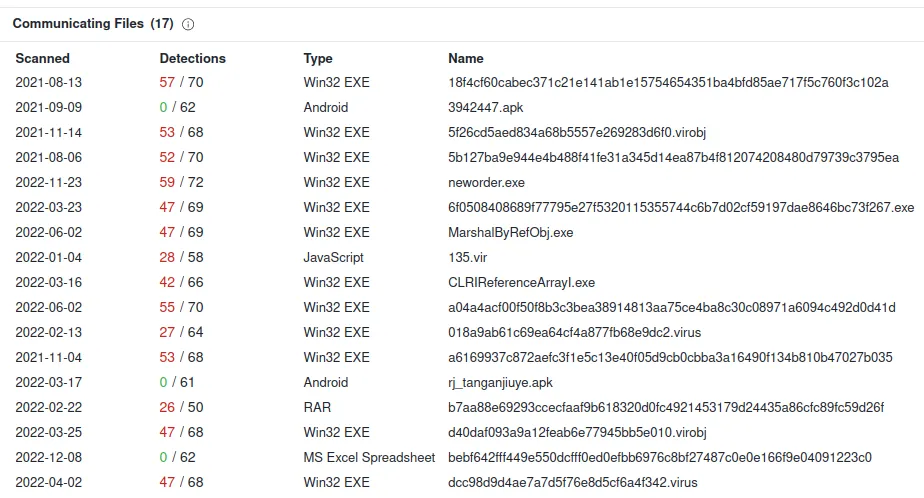
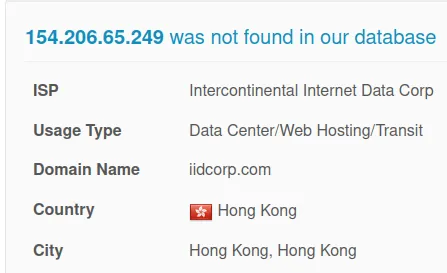
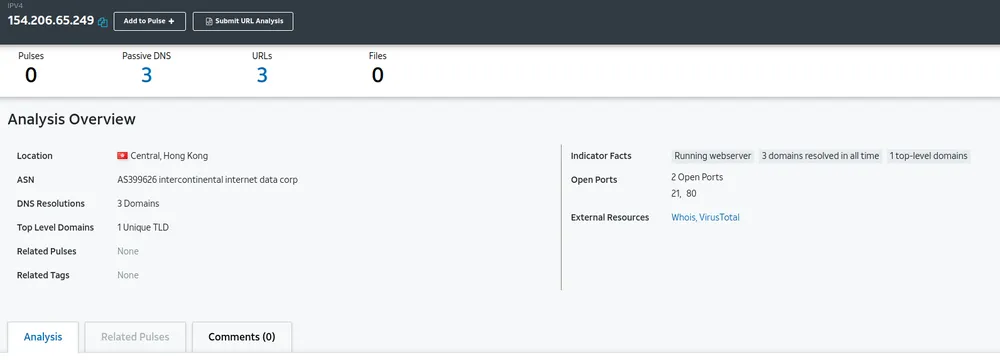
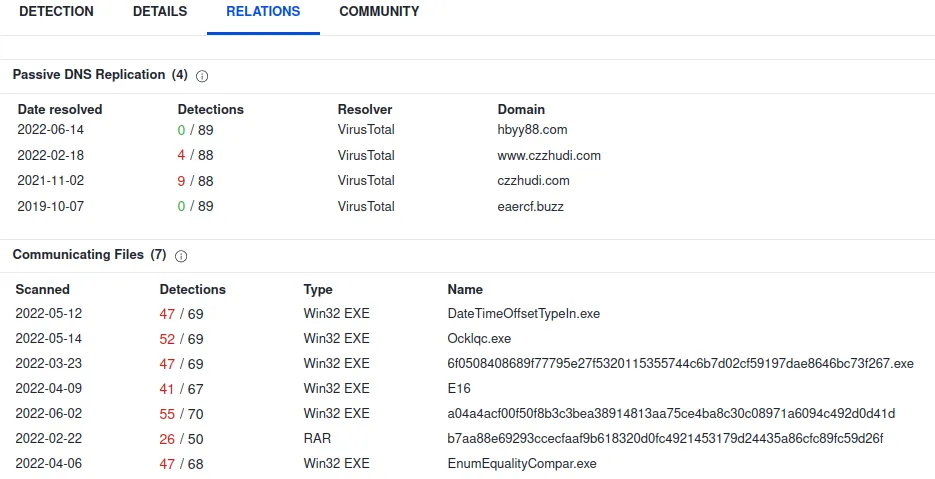
www[.]czzhudi[.]com
IP: 154.206.65.249
Verdict: Bad
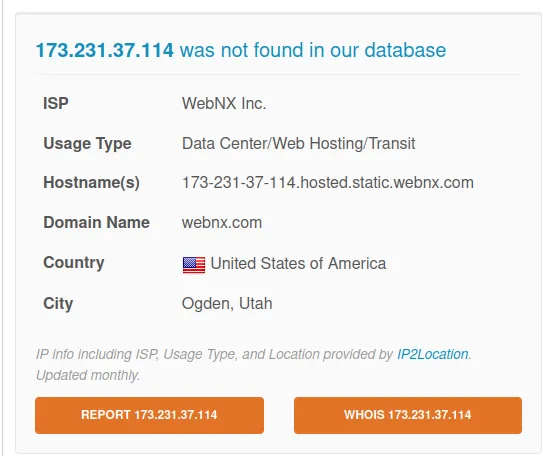
www[.]chinadqwx[.]com
IP: 173.231.37.114
Verdict: Bad
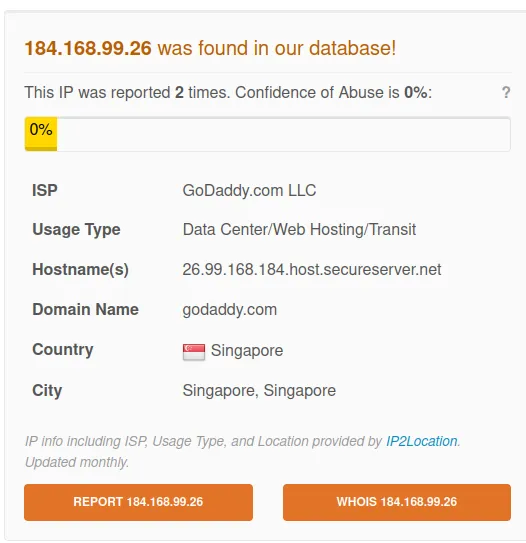
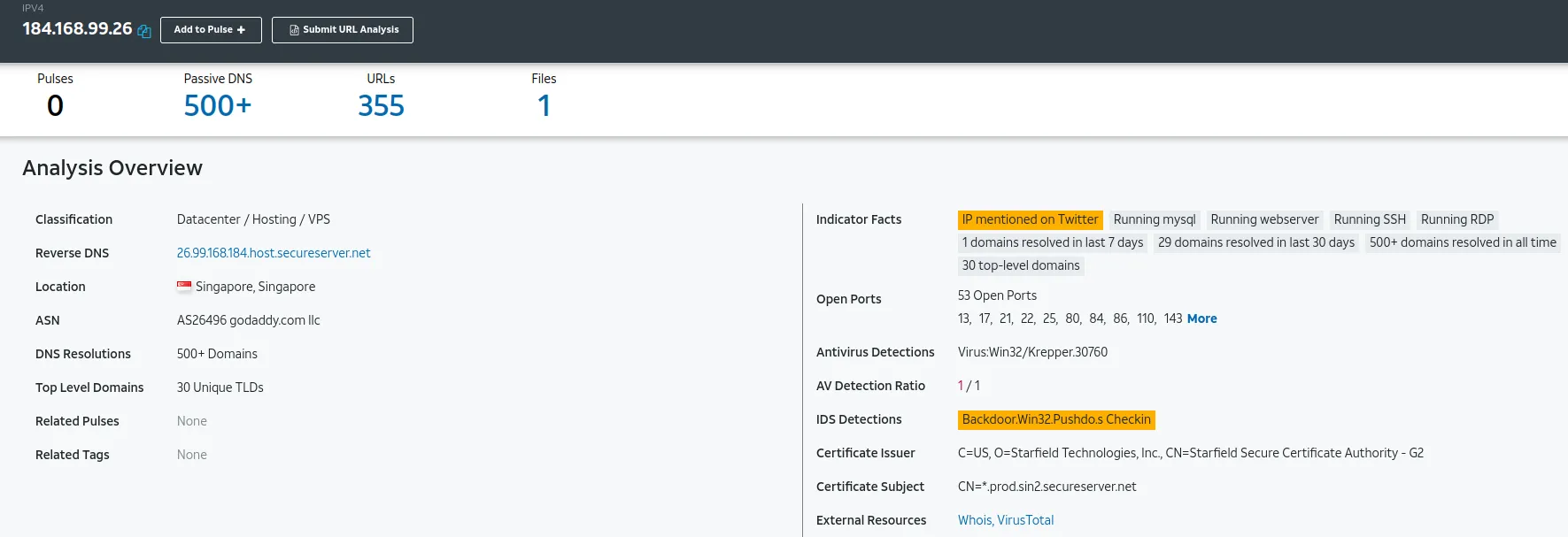
www[.]awridahmed[.]com
IP: 184.168.99.26
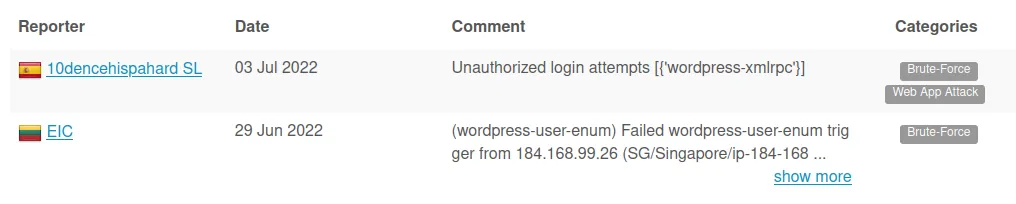
Verdict: Bad
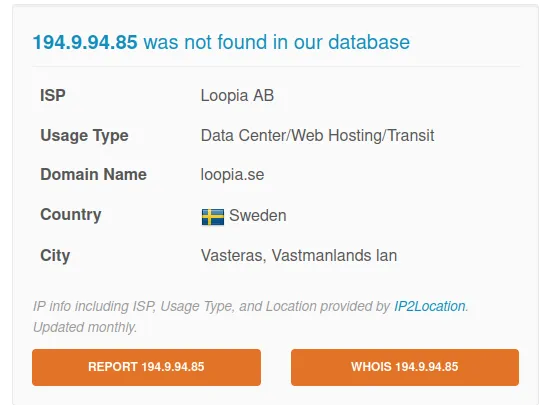
www[.]hentainftxxx[.]com
IP: 194.9.94.85
Verdict: Bad
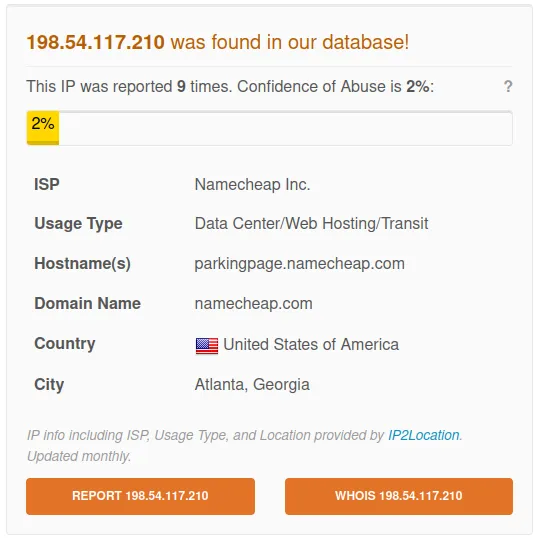
www[.]moonshot[.]properties
IP: 198.54.117.210
Verdict: Bad
www[.]campdiscount[.]info
IP: 198.54.117.215
AbuseIPDB: Bad
https://www.abuseipdb.com/check/198.54.117.215
AlienVault: Bad
https://otx.alienvault.com/indicator/ip/198.54.117.215
VirusTotal: Bad
https://www.virustotal.com/gui/ip-address/198.54.117.215
Verdict: Bad
www[.]jogoreviravolta[.]com
IP: 198.185.159.144
AbuseIPDB: Normal\
https://www.abuseipdb.com/check/198.185.159.144
Alienvault: Bad
https://otx.alienvault.com/indicator/ip/198.185.159.144
Virustotal: Bad
https://www.virustotal.com/gui/ip-address/198.185.159.144
Verdict: Bad
www[.]mystore[.]guide
IP: 209.17.116.163
AbuseIPDB: Bad
https://www.abuseipdb.com/check/209.17.116.163
AlienVault: Bad
https://otx.alienvault.com/indicator/ip/209.17.116.163
VirusTotal: Bad
https://www.virustotal.com/gui/ip-address/209.17.116.163
Verdict: Bad
www[.]xn–pckwb0cye6947ajzku8opzi[.]com
IP address: 142.251.40.147
AbuseIPDB: Normal
https://www.abuseipdb.com/check/142.251.40.147
AlienVault: Normal
https://otx.alienvault.com/indicator/ip/142.251.40.147
VirusTotal: Normal
https://www.virustotal.com/gui/ip-address/142.251.40.147
Verdict: Normal
www[.]elsiepupz[.]com
IP address: 216.58.193.147
AbuseIPDB: Normal
https://www.abuseipdb.com/check/216.58.193.147
AlienVault: Normal
https://otx.alienvault.com/indicator/ip/216.58.193.147
VirusTotal: Bad
https://www.virustotal.com/gui/ip-address/216.58.193.147
Verdict: Bad
www[.]globalsovereignbank[.]com
IP: 216.172.184.77
AbuseIPDB:
https://www.abuseipdb.com/check/216.172.184.77
Alienvault: Normal
https://otx.alienvault.com/indicator/ip/216.172.184.77
VirusTotal: Bad
https://www.virustotal.com/gui/ip-address/216.172.184.77
Verdict: Bad
Here is the list of malicious domains:
1. www[.]seo-python[.]com
2. www[.]keysine[.]com
3. www[.]db-propertygroup[.]com
4. www[.]katchybugonsale[.]com
5. www[.]ban-click[.]com
6. www[.]riskprotek[.]com
7. www[.]privilegetroissecurity[.]com
8. www[.]theperfecttrainer[.]com
9. www[.]hydrocheats[.]com
10. www[.]nt-renewable[.]com
11. www[.]czzhudi[.]com
12. www[.]chinadqwx[.]com
13. www[.]awridahmed[.]com
14. www[.]hentainftxxx[.]com
15. www[.]moonshot[.]properties
16. www[.]campdiscount[.]info
17. www[.]jogoreviravolta[.]com
18. www[.]mystore[.]guide
19. www[.]xn–pckwb0cye6947ajzku8opzi[.]com
20. www[.]elsiepupz[.]com
21. www[.]globalsovereignbank[.]com
Let’s find out what computer was infected.
Previously, we saw that most of the traffic came from 172.16.0.131. So what we can do is use the DHCP traffic to find the hostname.
So now we know that the hostname of 172.16.0.131 is DESKTOP-VD15107, and we got the mac address of that computer.
We can also look into the “NTLM” log to see who logs in using that desktop. We can also see that the user: tricia.becker is logged in on 2022-02-23T18:23:18 (6 pm), which would be 1 pm est.

Let’s see if we can find the file that hosted the malware
To do this: We shall move to Wireshark.
This is the display filter we’re going to use:
|
|
What this filter does is only show me only the malicious domain that I listed.

As we mentioned earlier, /uar3/ is a sign of the formbook. When we follow one of this malicious traffic, we get little information on the client side (red). Usually, that is a bad sign.


Furthermore, if we’re curious about what non-malicious traffic looks like, we can use this query:
(((http.request or tls.handshake.type eq 1) and !(ssdp))) && !(ip.dst in {216.172.184.77, 216.58.193.147, 213.186.33.5, 209.17.116.163, 198.185.159.144, 198.54.117.215, 198.54.117.210, 194.9.94.85, 184.168.99.26, 173.231.37.114, 154.206.65.249, 120.55.51.124, 104.21.89.147, 104.16.12.194, 72.167.191.69, 66.235.200.112, 66.29.145.216, 23.227.38.74, 3.130.253.23})
What this filter does is it gives you the domains that are NOT the following IP:

This is what regular traffic looks like:

In the image, this is windows update traffic.
Compared to the Malicious Domain:

We got little information.
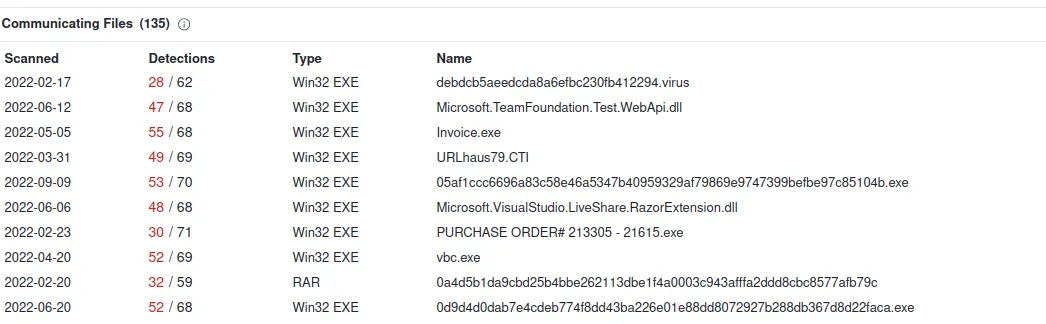
That’s nice, but what about finding malicious content downloaded to the desktop?
We can find that by going to file -> Export Object -> HTTP
We get a massive list of files and picture that was downloaded and transferred.

Suppose we were to go to one of these hostnames containing content-type: text/html. We would see something similar.

What was interesting is one of the malicious domains contained different languages of access denied

What is most interesting is that we have two unique files. One picture and one download application. Last time I check, people don’t name their files as long random text.

Let’s save it on our desktop and see what happens.
💡 Please note: When I’m opening these files, I’m doing it on my virtual machines, which are isolated from my network. Please be careful!
Before we start, let’s download some essential malware analysis tools.
|
|
Allow us to use strings. The strings allowed us to read text inside an application without executing it.
The next thing we want to install is a hex editor. This allows us to see if an image file is a .exe file by looking at the hex header. We are spotting for 4D 5A
sudo apt install hexyl
First installed, you have something like this:

We can look up the file signature of .xlsx and compare it to what we have.

Look like it is a .xlsx
Anyways, back to the actual program. We will download the two unique items we found and do some analysis. Make sure to change your network adapter to host only.

As we can see, the first row is all 0. This means that the picture is corrupt

As we can see, our windows executable is a .exe file (4d 5a)

Let’s run it and see what happens; I have a fresh copy just in case things go wrong.

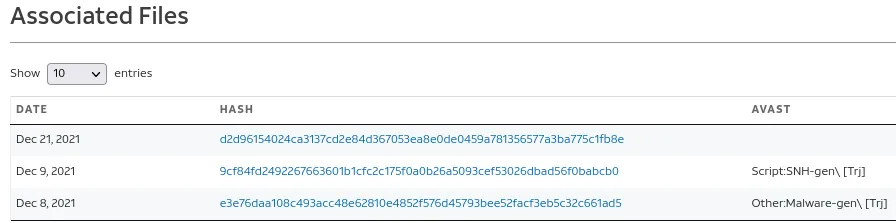
Well… Nothing happens. Let’s take the md5 hash of the exe before we reset to a new copy.
57595f82e73bed372c669e907d4db642
Wow, what an insane find. It looks like the malware is Emotet. You can read more information about Emotet here.
Here you can find a link to the dynamic analysis of the malware: https://app.any.run/tasks/4575f9ce-72c0-485f-ba37-a8ac43e5f458/
When the virus was first executed, It created a process name “rundll32.exe” and created a subprocess called “regsvr32.exe”
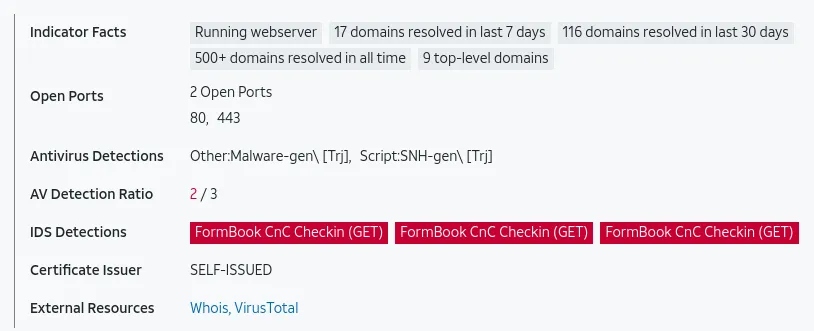
Then anyRun provides us with a list of potential C2 channels.
|
|
It is a long list, but we can find an easier way to find the C2 channel using RITA and Zeek. But it will help to cross-reference this list later on.
Finding the C2 Channel
So what is a C2 Channel?
- It is a centralized base that hackers use to relay commands to beacons and a way to gather information in one place.
Then what is a beacon?
- You can think of a beacon as a minion in part of a botnet. It will send a signal to the C2 channel asking if it has a command ready to execute, and it will check every x amount - depending on the hacker set it to.
So how do we detect beacons?
- One: by looking for long connections
- Two: Based on how often it checks back to base
- Three: Session size analysis - After a command is executed ->, information is retrieved (Increase in size). Then if you see a small packet size after the command is executed, you can treat it as additional command being executed.
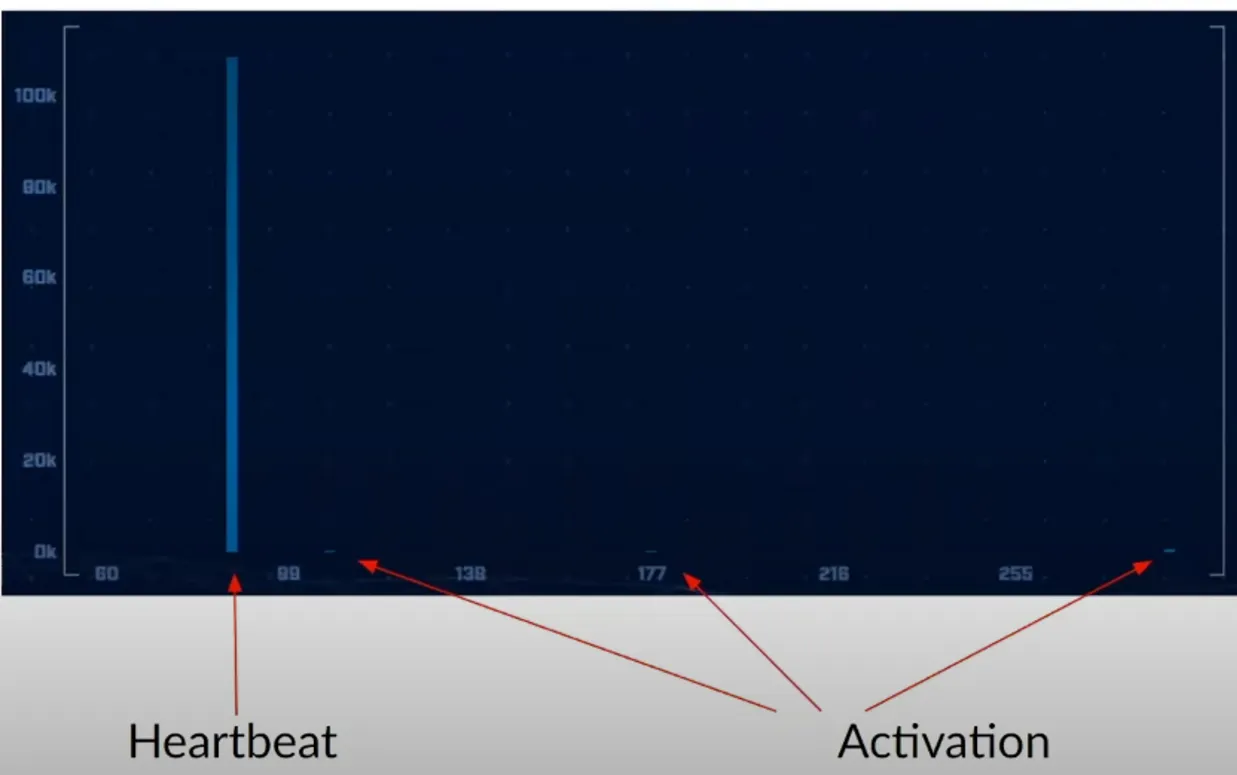
Source: https://www.activecountermeasures.com/hunt-training/
Now, let’s find a potential c2 channel using RITA.
Here I only have my pcap file of the malicious traffic. What I’m going to do is let zeek ingest this pcap file.
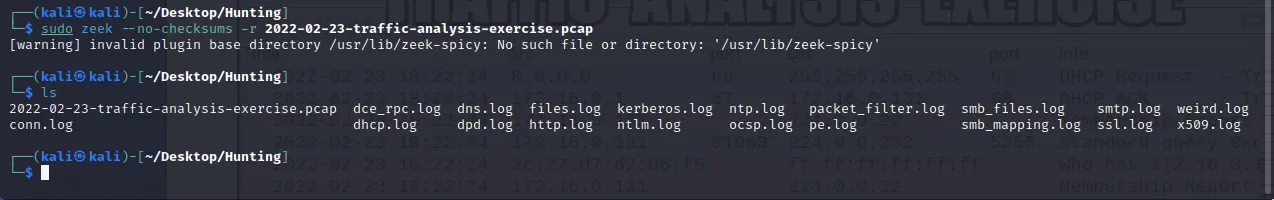
Then use all these to create a Rita database.
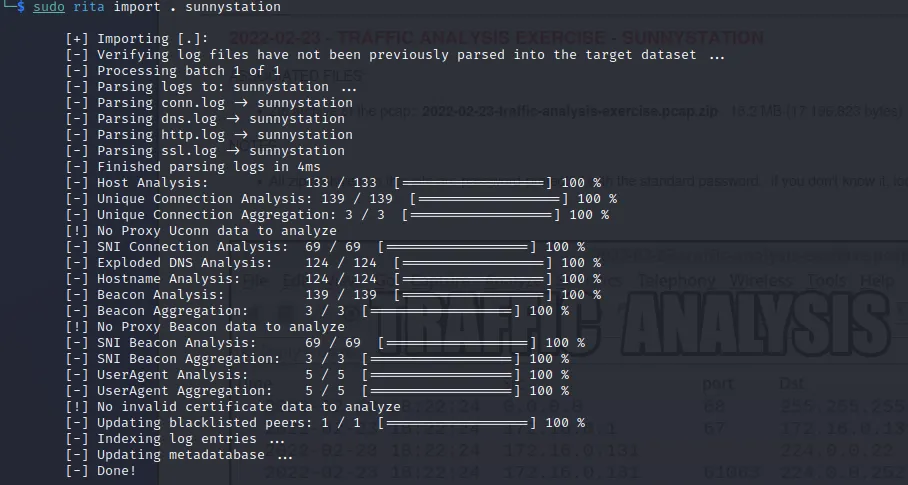
Now we’re ready to find some c2 channels.
Let’s start by finding the long connections.
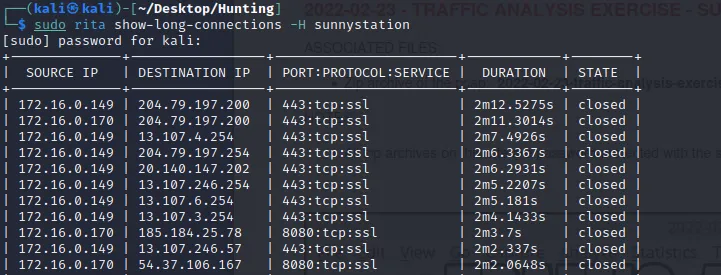
From the chart, the longest connection was made to:
- 204.79.197.200
- 13.107.4.254
- 204.79.197.254
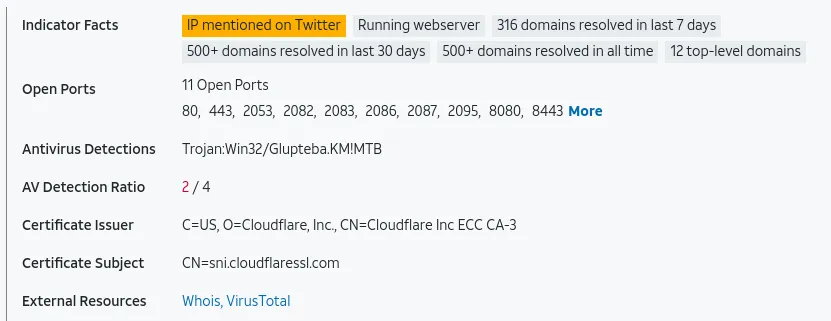
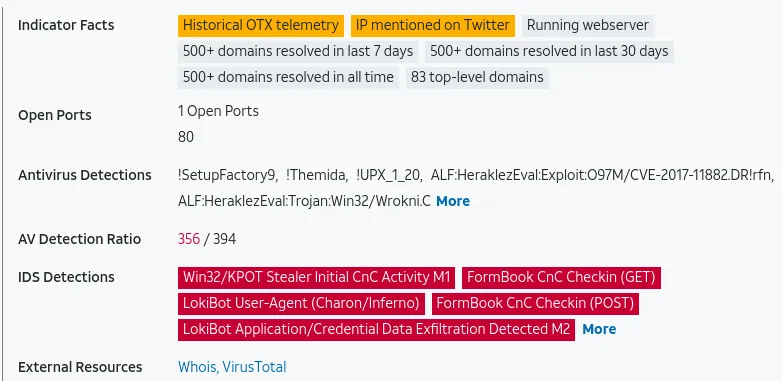
Another helpful feature that RITA has is to print blocklisted IPs that received connections (These could be well-known IPs that C2 uses)
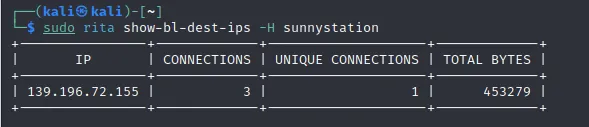
If we look up: 139.196.72.155, We can see what the C2 is.
https://www.virustotal.com/gui/ip-address/139.196.72.155/relations
According to VT, it emotet which explains the executable we found earlier:
57595f82e73bed372c669e907d4db642
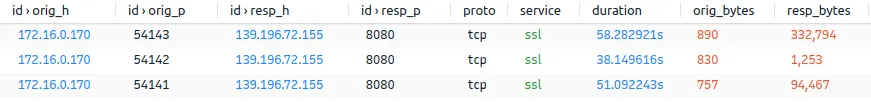
Earlier, we said that our victim’s computer was 172.16.0.131. Now we have to add 172.16.0.170 to the list. Let’s find more information about this IP in our network by going to the DHCP log.
MAC address: 00:12:f0:64:d1:d9
Hostname: DESKTOP-W5TFTQY
IP: 172.16.0.170
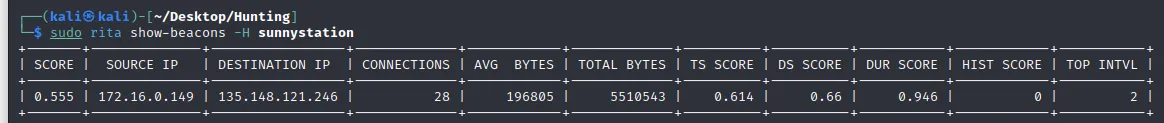
Now, let’s find the beacons communicating to the C2 server using one of the following commands:
The score is 0.55, which is 55%, a deficient score when determining for beacons. Not only that, the 135.148.121.246 is not even on the list for long connections. So chances of this IP being a C2 server are low.
Conclusion
The goal of incident response:
|
|
- List of hosts/user account to isolate:
- 172.16.0.170, Hostname: DESKTOP-W5TFTQY
- 172.16.0.131, Hostname: DESKTOP-VD15107
- 172.16.0.149, Hostname: DESKTOP-KPQ9FDB
2. What type of malware are they infected with?
- Emotet, Formbook
IOC (Indicator of Compromise):
- HTTP traffic of /uar3/
zbBYgukXYxzAF2hZc.exe- Suricata Alerts of Formbook
- Connection to Emotet C2 server
Malicious Domain:
1. www[.]seo-python[.]com
2. www[.]keysine[.]com
3. www[.]db-propertygroup[.]com
4. www[.]katchybugonsale[.]com
5. www[.]ban-click[.]com
6. www[.]riskprotek[.]com
7. www[.]privilegetroissecurity[.]com
8. www[.]theperfecttrainer[.]com
9. www[.]hydrocheats[.]com
10. www[.]nt-renewable[.]com
11. www[.]czzhudi[.]com
12. www[.]chinadqwx[.]com
13. www[.]awridahmed[.]com
14. www[.]hentainftxxx[.]com
15. www[.]moonshot[.]properties
16. www[.]campdiscount[.]info
17. www[.]jogoreviravolta[.]com
18. www[.]mystore[.]guide
19. www[.]xn–pckwb0cye6947ajzku8opzi[.]com
20. www[.]elsiepupz[.]com
21. www[.]globalsovereignbank[.]com
C2 control:
- 139.196.72.155